In this article I will walk us throught installing a bare metal owncloud server based on ubuntu server 18.04. Throughout this guide we will assue that our server is named myowncloud.mydomain.com.
Base system installation
First steps as usual, we download the ubuntu server install image. If you wish to use full disk encryption, please use the "alternate installer" ubuntu-18.04.x-server-amd64.iso images instead of the "standard" ubuntu-18.04.x-live-server-amd64.iso images that do not currently support advanced LVM options. Next, "burn" the iso on a USB stick and boot it.
Now, if you wish to use full disk encryption, in the "Partition disks" step select: "Guided - user entire disk and setup encrypted LVM".
During installation I also chose the "Install security updates automatically" option. As for the software selection (tasksel), I only picked the "OpenSSH server" option as I wished to install everything else manually.
System preparation
After installation is complete, boot the new system and log on to it.
Let's first bring everything up to date and install a firewall.
apt update
apt upgrade -y
apt dist-upgrade -y
#firewall
ufw allow OpenSSH
ufw enable
If you did not setup unattended package upgrades during installation you may do so now.
apt install unattended-upgrades
dpkg-reconfigure -p low unattended-upgrades
OwnCloud prerequisites
Next we will install the owncloud prerequisites in addition to some nice-to have packages like vim and tmux. We will also update our firewall to allow ports 80 and 443 to pass through to apache.
apt-get install \
apache2 \
curl \
mysql-server \
php libapache2-mod-php php-mysql \
certbot python-certbot-apache \
vim tmux wget unattended-upgrades \
php-bz2 php-curl php-gd php-imagick php-intl php-mbstring \
php-xml php-zip php-redis redis
ufw app list
ufw app info "Apache Full"
ufw allow "Apache Full"
Install dyndns update script
In my case, I needed to setup dynamic DNS for my server. To do that I chose the excelent FreeDNS service that allows you to update your IP using a simple http request done through wget. Go here to get the command for your address.
So we now edit the crontab to add the updates:
crontab -e
# Add the following lines:
#@hourly sleep 12 ; wget -O - http://freedns.afraid.org/dynamic/update.php?SOME_HASH_HERE >> /tmp/freedns_owncloud.log 2>&1 &
#@reboot sleep 12 ; wget -O - http://freedns.afraid.org/dynamic/update.php?SOME_HASH_HERE >> /tmp/freedns_owncloud.log 2>&1 &
Run certbot to get SSL certificates
Now that we have our DNS up and running, we need to use certbot to get SSL certificates for our server. This is crucial since using owncloud over the internet without SSL encryption would allow anyone to read our login information and exchanged files. Not a good idea obviously. This is more or less what you should see during this process. At this point, to be able to run certbot, you must configure your router to allow acessing ports 80 and 443 of your server from the internet.
certbot
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): ****REMOVED****@mailserver.com
-------------------------------------------------------------------------------
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v01.api.letsencrypt.org/directory
-------------------------------------------------------------------------------
(A)gree/(C)ancel: A
No names were found in your configuration files. Please enter in your domain
name(s) (comma and/or space separated) (Enter 'c' to cancel): myowncloud.mydomain.com
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for myowncloud.mydomain.com
Enabled Apache rewrite module
Waiting for verification...
Cleaning up challenges
Created an SSL vhost at /etc/apache2/sites-available/000-default-le-ssl.conf
Enabled Apache socache_shmcb module
Enabled Apache ssl module
Deploying Certificate to VirtualHost /etc/apache2/sites-available/000-default-le-ssl.conf
Enabling available site: /etc/apache2/sites-available/000-default-le-ssl.conf
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
-------------------------------------------------------------------------------
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
-------------------------------------------------------------------------------
Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2
Enabled Apache rewrite module
Redirecting vhost in /etc/apache2/sites-enabled/000-default.conf to ssl vhost in /etc/apache2/sites-available/000-default-le-ssl.conf
...
Now that we got our SSL certificates, we need to configure cron to renew them periodically, as these certificates expire every 3 months. We also need to restart apache after the certificates have been removed.
crontab -e
@daily /usr/bin/certbot renew -n --post-hook "systemctl reload apache2"
Secure mysql server
Run:
mysql_secure_installation
Follow the prompts to setup a secure mysql password and remove test databases/users and disable remote root logins.
Get latest version of owncloud
Go to the owncloud downloads page and get the URL of the latest owncloud tarball.
cd /var/www
wget https://download.owncloud.org/community/owncloud-10.1.1.tar.bz2
tar xjf owncloud-10.1.1.tar.bz2
# Change ownership of owncloud files
find /var/www/owncloud \( \! -user www-data -o \! -group root \) -print0 | xargs -r -0 chown www-data:root && \
chmod g+w /var/www/owncloud
# Make data directory
mkdir /mnt/owncloud_data
chown www-data:root /mnt/owncloud_data && chmod g+w /mnt/owncloud_data
Configure apache
First configure the default servername for apache.
# Add this line near the end of the file:
# ServerName myowncloud.mydomain.com
vim /etc/apache2/apache2.conf
Now edit /etc/apache2/mods-enabled/dir.conf to give precedence to php files by bringing index.php in front of the rest of the file types.
vim /etc/apache2/mods-enabled/dir.conf
Next, we need to edit our apache configuration. First find the configuration file for the owncloud website:
apache2ctl -t -D DUMP_VHOSTS | grep myowncloud.mydomain.com
In my case that is /etc/apache2/sites-enabled/000-default-le-ssl.conf.
Now enable the mod_headers apache plugin and then edit the website config file.
a2enmod headers # Enable mod_headers
vim /etc/apache2/sites-enabled/000-default-le-ssl.conf
Within the config file add the following under the
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=15552000; includeSubDomains"
</IfModule>
and set:
DocumentRoot /var/www/owncloud
Finally, restart apache:
systemctl restart apache2
Configure php for production
Make sure the following options in /etc/php/7.2/apache2/php.ini are set as below to reduce unintended information exposure through debugging messages:
display_errors = Off
display_startup_errors = Off
Also you may want to edit /var/www/owncloud/.user.ini to increase some
limits. Mine currently reads:
upload_max_filesize=1025M
post_max_size=1025M
memory_limit=1024M
mbstring.func_overload=0
always_populate_raw_post_data=-1
default_charset='UTF-8'
output_buffering=0
Configure mysql owncloud user and privileges
Use your own uniqueue_password for the owncloud user here
mysql -u root -p <<SCRIPT
CREATE DATABASE owncloud;
GRANT ALL ON owncloud.* to 'owncloud'@'localhost' IDENTIFIED BY 'uniqueue_password';
FLUSH PRIVILEGES;
SCRIPT
You will also need to provide the root user mysqpassword that you had set previously
Configure cron to run owncloud-scheduled jobs
crontab -u www-data -e
Add the line:
*/15 * * * * php -f /var/www/owncloud/cron.php
Configure owncloud through web interface
It is now time to configure owncloud through the web interface. Point your browser to http:://myowncloud.mydomain.com
Use the following data:
- username: Choose one
- password: Choose a strong one
- data folder: /mnt/owncloud_data
- database: MySql/MariaDB
- database_user: owncloud
- database_password: the one you used in the "Configure mysql owncloud user and privileges" step
- database_name: owncloud
- database_host: localhost
Now once the configuration succeeds, use the username and password that you just configured to log in. You will be transferred to the Admin General Settings page. From there, configure owncloud to use the system cron and then review your pending security and setup warnings. At this point, mine were:
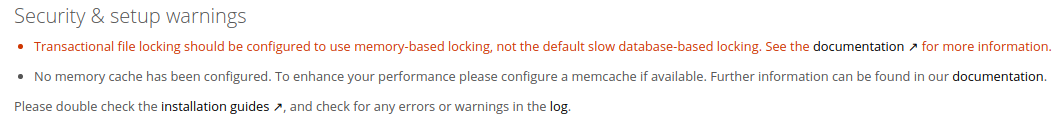
Which both should be resolved once we configure redis.
Activate redis as a cache
Edit /var/www/owncloud/config/config.php and add the following settings:
'memcache.locking' => '\OC\Memcache\Redis',
'memcache.local' => '\OC\Memcache\Redis',
'redis' => [
'host' => 'localhost',
'port' => 6379,
],
Now all your security and setup warnings should be resolved.
Fail2ban
Fail2ban is a security system that monitors the system logs and manipulates the system firewall on the fly to block hosts that send suspicious requests. We will proceed to install and configure fail2ban to block for 30 minutes, hosts that have more than 5 failed login attempts within the last 10 minutes.
apt install fail2ban
For fail2ban to work correctly, the owncloud log entries must be in the correct time zone. Check the system time zone and set it correctly in
the owncloud config.php.
# cat /etc/timezone
Europe/Athens
# vim /var/www/owncloud/config/config.php
...
'logtimezone' => 'Europe/Athens',
...
cp /etc/fail2ban/fail2ban.conf /etc/fail2ban/fail2ban.local
Create a filter and jail for owncloud
cat > /etc/fail2ban/filter.d/owncloud.conf <<OWNCLOUD_FILTER
[Definition]
failregex={"reqId":".*","level":2,"time":".*","remoteAddr":".*","user":".*","app":"core","method":".*","url":".*","message":"Login failed: '.*' \(Remote IP: '<HOST>'\)"}
ignoreregex =
OWNCLOUD_FILTER
cat > /etc/fail2ban/jail.d/owncloud.conf <<OWNCLOUD_JAIL
[owncloud]
enabled = true
port = 80,443
protocol = tcp
filter = owncloud
maxretry = 5
findtime = 600
bantime = 1800
logpath = /mnt/owncloud_data/owncloud.log
OWNCLOUD_JAIL
service fail2ban restart
service fail2ban status
Now check your configuration by attempting to log in to owncloud 5 times in a row with wrong credentials.
occ
Owncloud provides the occ console application to run several administrative tasks. Occ is a php script that needs to run as the ww-data user. For instance, you can use the following command to get a status report from the owncloud server:
sudo -u www-data php /var/www/owncloud/occ status
Many more useful commands exist so do check the documentation.